Leading Tips for Ensuring Secure Data Destruction in Your Cyber Security Strategy
Leading Tips for Ensuring Secure Data Destruction in Your Cyber Security Strategy
Blog Article
Discovering the Relevance of Information Damage in the Context of Computer Safety Services and Protecting Confidential Data
In an age where information breaches are significantly typical, the importance of reliable data damage can not be overemphasized. Organizations should take on strict steps to guarantee that sensitive information is not only secured during its lifecycle yet additionally emphatically eliminated when no longer needed. The approaches employed for information eradication, paired with conformity to legal requirements, play a critical role in keeping discretion and depend on. The implications of these methods expand beyond plain conformity, affecting a firm's credibility and functional stability in the digital market. What strategies can organizations apply to boost their information destruction protocols?
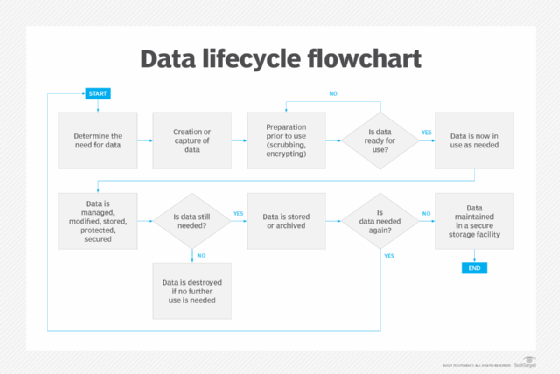
Recognizing Information Damage
Information destruction is a crucial part of computer protection that entails the long-term removal of information from storage space devices to stop unauthorized access and prospective information breaches. In a progressively digital landscape, organizations face heightened dangers connected with delicate details being incorrectly accessed or made use of. Efficient data destruction safeguards versus these dangers, guaranteeing that confidential dataâEUR" such as customer information, intellectual residential property, and financial recordsâEUR" can not be recouped after disposal.
Understanding the relevance of information devastation prolongs past mere conformity with governing and legal frameworks; it is crucial for keeping organizational integrity and trust fund. When information is improperly taken care of or improperly damaged, the consequences can be severe, including monetary loss, reputational damages, and legal responsibilities.

Methods of Data Elimination
One prevalent method is data wiping, which includes overwriting existing information with random patterns several times. This technique makes the original information irretrievable, making it a prominent choice for companies seeking to safeguard confidential information.
One more method is degaussing, which makes use of a powerful magnetic field to interrupt the magnetic domains on storage space devices, successfully erasing the data. This method is specifically effective for magnetic media but is not suitable to solid-state drives.
Physical destruction is an additional robust method, crushing or entailing the shredding of storage space devices. This technique guarantees that information recuperation is basically difficult, making it perfect for very sensitive info.
Lastly, security can function as a corresponding approach to data eradication. By securing information before removal, organizations can include an additional layer of security, making certain that also if remnants are recuperated, they remain inaccessible without the decryption secret. Each technique needs to be picked based upon the degree of information sensitivity and the certain security demands of the organization.
Legal Compliance and Information Safety
Organizations should navigate a complicated landscape of lawful demands connected to data protection, especially after navigate to this site implementing approaches of information eradication. Various guidelines, such as the General Data Defense Regulation (GDPR) and the Medical Insurance Portability and Responsibility Act (HIPAA), impose strict standards on just how organizations should manage and dispose of delicate information. Failing to follow these guidelines can bring about significant lawful repercussions, consisting of considerable penalties and reputational damages.
Data destruction processes have to be meticulously recorded to demonstrate conformity with appropriate laws and criteria. This paperwork not just works as proof of adherence to lawful obligations however likewise illustrates a dedication to securing sensitive info. Organizations needs to also develop clear policies regarding data retention and damage timelines, ensuring that information is not held longer than essential.

Moreover, regular audits and assessments of information devastation techniques are necessary to maintain conformity and adjust to advancing lawful structures (data destruction). By proactively resolving legal requirements, organizations can mitigate dangers connected with data violations and demonstrate their dedication to information security. Eventually, prioritizing lawful compliance in information devastation procedures is not simply a regulatory obligation, but a fundamental element of a robust information safety and security strategy
Influence on Business Online Reputation
The online reputation of a business can be substantially influenced by its method to data devastation and monitoring. In today's digital landscape, where information violations can occur at any moment, the failing to appropriately throw away delicate info can lead to extreme consequences. Organizations that improperly manage data destruction danger revealing confidential consumer info, which not only breaches privacy laws but likewise deteriorates depend on among stakeholders and customers.
A ruined credibility can lead to reduced customer commitment, as customers end up being hesitant to engage with a company that has shown negligence in shielding their data. Adverse publicity directory bordering an information violation can have a long lasting impact, as potential consumers could be deterred by the perceived absence of security. This can cause a straight decrease in revenue and market share.
Moreover, organizations that prioritize data damage as component of their protection approach can enhance their credibility by showcasing their dedication to securing sensitive information. By taking on stringent data administration methods, organizations can not only alleviate threats yet additionally position themselves as reliable entities in their respective markets, thereby strengthening their overall brand name photo.

Ideal Practices for Secure Disposal
Implementing best practices for protected disposal of information is necessary for alleviating risks associated with data breaches and guaranteeing conformity with privacy regulations. Organizations must take on a thorough data disposal plan that describes treatments for both physical and digital information destruction.
For physical information storage space devices, such as hard disk drives, shredding or degaussing is suggested to stop data recovery. Furthermore, companies need to preserve a chain of protection documents throughout the disposal process, ensuring accountability and traceability of disposed items.
For digital data, making use of software that complies with sector criteria for data wiping is crucial. This software needs to overwrite existing information several times, making recovery practically impossible. It is also crucial to confirm the effectiveness of the information destruction process via audits or third-party evaluations.
Training employees on secure disposal methods includes one more layer of safety and security, as human error can usually lead to information exposure. Regularly assessing and updating disposal plans makes sure positioning with advancing laws and technological improvements. By executing these ideal methods, companies can substantially minimize the danger of unapproved data accessibility and improve their total information security method.
Verdict
In conclusion, information devastation is an essential facet of computer system safety and security services that makes sure the defense of confidential information from unapproved accessibility. Implementing efficient techniques of data eradication, sticking to legal conformity, and identifying the effect on organization track record are important elements of a detailed information security approach. By taking on finest practices for safe disposal, organizations can cultivate trust with clients and guard sensitive information, ultimately adding to a much more safe electronic landscape.
In an era where information violations are significantly usual, the significance of effective data destruction can not be overstated.Data devastation is an essential element of computer system safety that involves the long-term elimination of data from storage devices to prevent unapproved access and potential information breaches. Organizations should additionally develop clear policies relating to data retention and destruction timelines, making sure that data is not held longer than needed.
By proactively resolving lawful demands, companies can reduce threats connected with information breaches and demonstrate their commitment to information security (data destruction). Eventually, focusing on legal conformity in data damage procedures is not simply a governing obligation, yet an essential facet of a click here for more info robust data safety and security method
Report this page